Electronically signed documents, just like physical ones, need to be taken care of. Although the concept of care in both cases differs, with e-signed documents one of the most important things is their validity span. Here you’ll find everything you need to know about making sure your signed documents remain valid in the long term.
Why long-term signature validity matters
How to ensure long-term validity of electronically signed documents? Will the signature become invalid when the signature certificate expires? These questions arise because usually signature certificates have a shorter life span than the need to save signed documents. Therefore, it is important to make sure signatures remain valid even after the signature certificate expires.
Let’s say you sign an NDA agreement. It needs to be saved for 10 years in your company. However, the certificate of electronic signature is only valid for 3 years. So technically an attempt to validate the signatures after those 3 years can be somewhat troublesome. The undeniable (or so called non–repudiable) fact is that the signature was valid at a previous point in time. So how to prove it?
This is taken care by two elements: a timestamp and signature certificate revocation data.
Timestamps are used to specify time till when signature was created, this way ensuring that the signature and signed document can’t be altered since the time recorded. Read more about timestamps here.
Although including timestamp is a good first step, it is not sufficient information for a relying party to validate the signature in the future. To make it valid in the long term, the signature needs to include signature certificate revocation data which ensures that at the time of signing signature certificate was truly valid.
So in short, long-term preservation of signatures is needed to be able to check signature’s validity long after all the certificates have expired.
Signature security levels and their meaning
To understand how signature validity works, we need to look into formats and security levels of signatures.
There are different formats of electronic signatures: XAdES, PAdES and CAdES. They are divided into 3 groups based on document formats. Electronic documents come in different formats and they can be either country specific or international. E.g., there are container based formats like ADoc in Lithuania, EDoc in Latvia, BDoc in Estonia, and a standard in the entire EU: ASiC and PDF. So each document format has a corresponding signature format: ASiC, ADoc, BDoc, EDoc documents use XAdES signatures, meanwhile PDF use PAdES signatures.
Based on a format, signature security levels are defined. For the sake of clarity, let’s divide them into tiers.
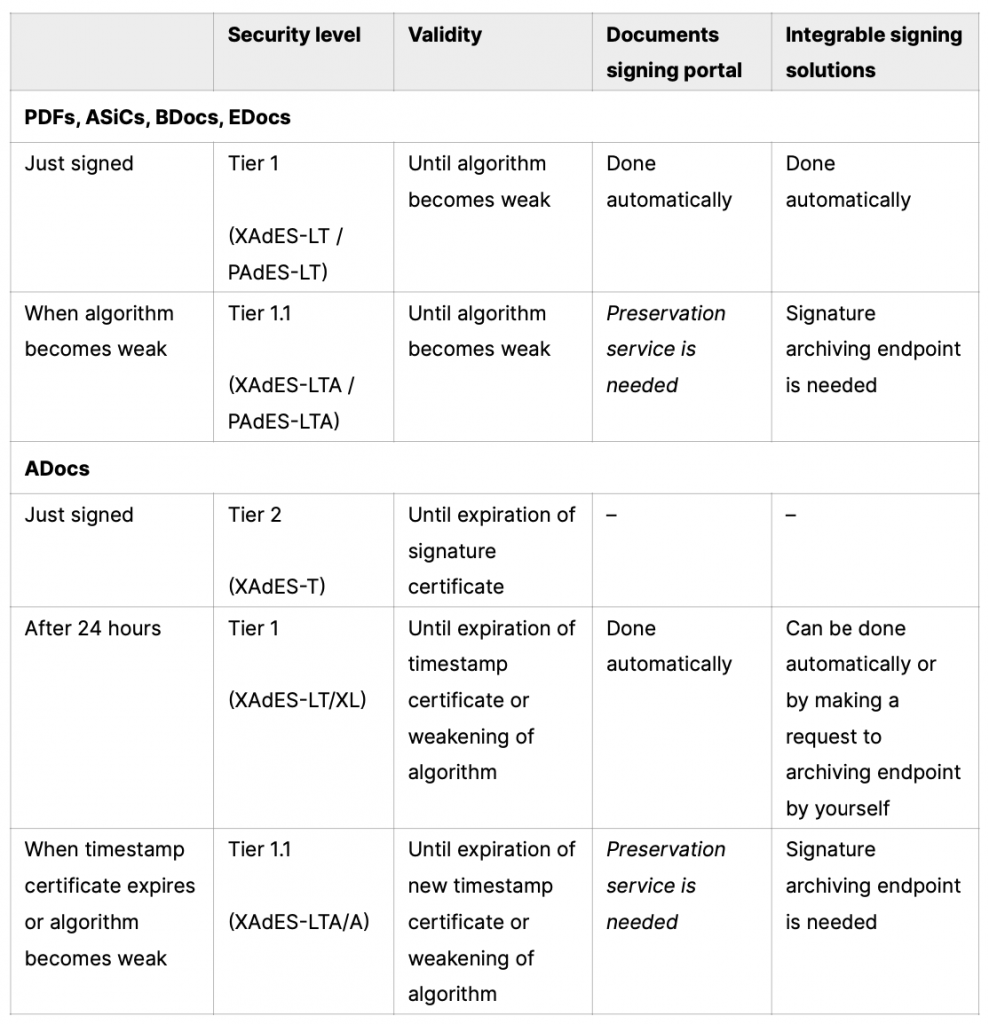
- Tier 3 (XAdES-B and PAdES-B): Basic Electronic Signature. It’s the lowest and simplest version that has no additional signature security measures. Tier 3 level signatures are valid until the end of signature certificate validity period or until the certificate is revoked which can happen even before its expiration date. Certificates can be revoked when changing your eID tool (e.g., when your surname changes), when it’s lost, due to security issues, etc.
- Tier 2 (XAdES-T and PAdES-T): Signature with a timestamp. A timestamp regarding the time of signing is added to protect against repudiation. Tier 2 level signatures are valid until the end of signature certificate validity period, and in this case certificate revocation doesn’t have any impact.
- Tier 1 (XAdES-LT/XL and PAdES-LT): Signature with Long Term Data. Certificates and their revocation data are embedded to allow verification in future even if their original source is not available. Tier 1 level signatures are valid until signing hash algorithms become weak. The European Union Agency for Cybersecurity (ENISA) is responsible for announcing this information. What does the weakening of algorithms mean? The strength of the hash algorithm used in signing is a critical element of the security. Weaknesses in hash algorithms can lead to situations in which attackers can tamper with or forge a signed document. Fun fact: up until now, there are 2 known algorithms that were announced and are now treated as insecure, MD5 got this status in 2012 and SHA-1 in 2017.
- Tier 1.1 (XAdES-LTA/A and PAdES-LTA): Signature with Long Term Data and Archive timestamp. By using periodical timestamping, compromising is prevented which could be caused by weakening previous signatures during a long-time storage period. So Tier 1.1 level signatures are basically the same as Tier 1, it just means that in a very long run, each time algorithms get weak, signature validity is extended once again, until the next time the algorithm is announced to no longer be secure.
Security with Dokobit
Depending on document format, default signature security levels on Dokobit vary.
When signing PDFs, ASiCs, BDocs, EDocs
On most document formats – PDFs, ASiCs, BDocs and EDocs – Dokobit solutions ensure Tier 1 level security. When you sign a document, initially the signature security is at Tier 3, we then uplift it automatically to Tier 1 by adding both a timestamp and signature revocation status.
This means that signatures on your documents will be valid until it is officially announced that signing hash algorithms are no longer secure. There is no clear deadline for when this can happen but we constantly monitor the situation and inform our customers about these changes.
If this happens, what should you do?
- If you’re using our documents signing portal, we suggest looking for a qualified preservation service that will help you uplift signature security level. The entire list of providers can be found in this EU Trust Services list.
- If you’re using our integrable signing solutions, you can take care of signature security level uplift on your own. If you have to store your documents in the long term, then you can set up long-term preservation functionality when integrating the solution or any other time before the algorithm becomes weak.
It is worth mentioning that in our integrable APIs responses, we include the information on what algorithms were used in a particular signature, so by saving this information in your systems, you can then easily find the documents the validity of which need to be extended. This means that you can monitor cryptographic risks by yourself or rely on our notification.
When signing ADocs
If you are signing ADocs, the situation differs a little bit.
- If you’re using our documents signing portal with any of the paid plans, then Tier 2 level security is ensured. When you sign a document, initially the signature security is at Tier 3, we then uplift it automatically to Tier 2 by adding a timestamp. As ADocs work in a different way, uplift to Tier 1 happens ~24 hours after the signature is created. 24 hours is a so-called grace period during which the certificate can be revoked, if this doesn’t happen, it means that the signature is valid and we can then include signature revocation status and this automatically uplifts signature to Tier 1 level. This means that it is valid until the expiration date of a timestamp certificate, which is usually 4-5 years. In this case another uplift is needed a few months before timestamp certificate expiration date or when the algorithm gets weak. Should you need to keep the document for a longer period, we suggest looking for a qualified preservation service that will help you uplift signature security level. The entire list of providers can be found in this EU Trust Services list.
- If you’re using our integrable signing solutions, you need to take care of signature security level uplift on your own. If you have to store your documents in the long term, then you can set up long-term preservation function when integrating the solution or any other time before the expiration date of timestamp certificate or before the algorithm becomes weak.
It is worth mentioning that in our integrable APIs responses, we include the information on what algorithms were used in a particular signature, so by saving this information in your systems, you can then easily find the documents the validity of which need to be extended. This means that you can monitor cryptographic risks by yourself or rely on our notification.
Here’s a full comparison in one place: